We have a prototype!
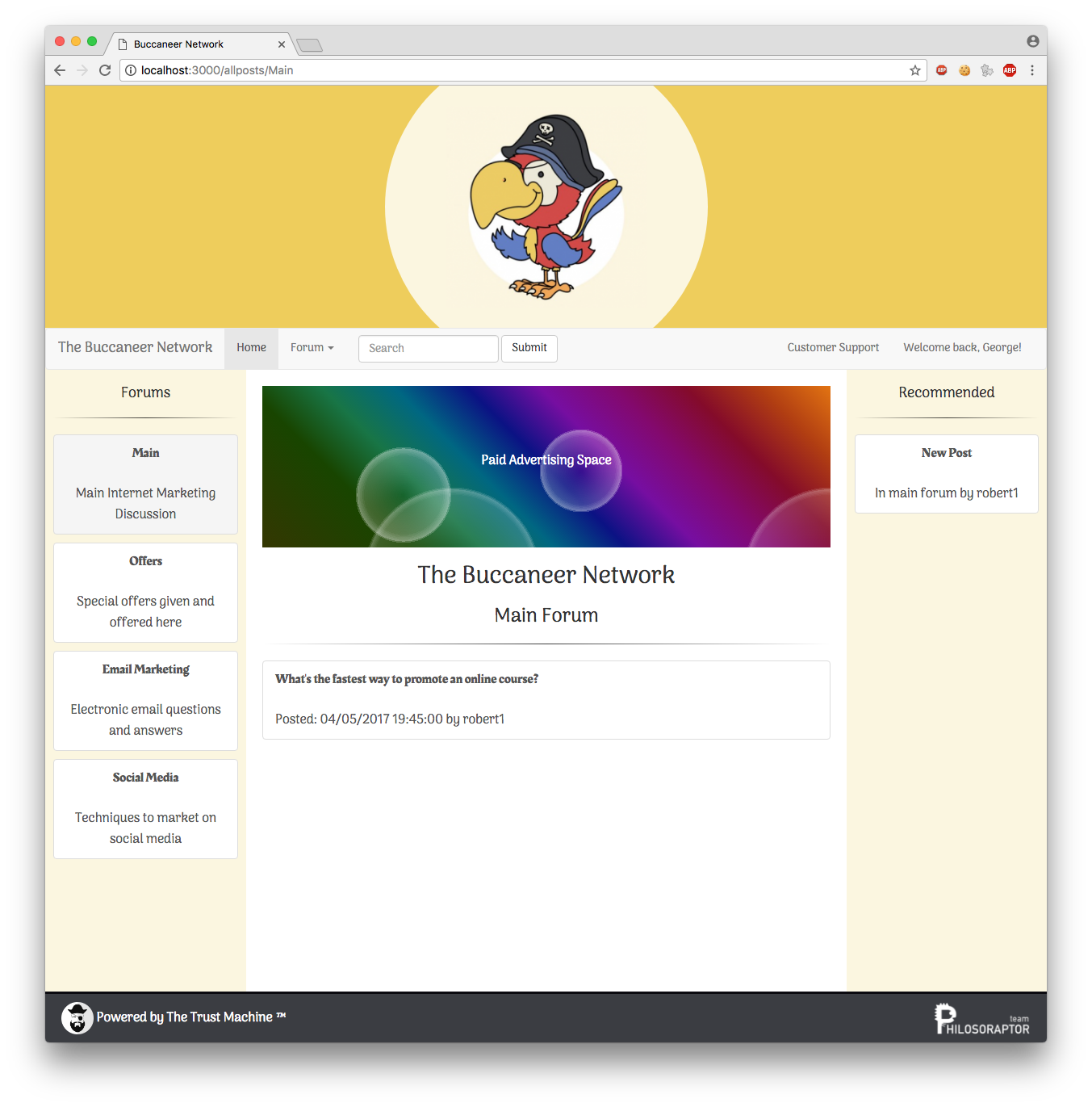
This mock up is a very, very basic mock-up of what could be achieved if this project were to go ahead.
You can visit it here.

We have a prototype!

This mock up is a very, very basic mock-up of what could be achieved if this project were to go ahead.
You can visit it here.
Trust, as we have seen, is a complex thing to model. To quantify it we need to look at a variety of parameters e.g. User behaviours, user provenance and user context. Each of these parameters will modify the trust value. However not all will be used in every setting. We will need different flavours of trust calculation and ways of keeping track of which was used to construct each trust calculation. Designing code to implement a complex model of trustworthiness is going to be a challenge, particularly if we want maintainable code built along proper Object Oriented design principles. Continue reading
By the time The Buccaneer Network launches it will already have a thriving community and the trust machine will be actively disrupting the industry. We will accomplish this in two ways. Firstly, we will take a page out of Stack Overflow’s playbook and build a solid community before the official launch. We will do so by inviting some of the most outspoken opponents of the incumbent operators to take part in our closed beta. At a very general level people automatically support that which they had a hand in creating. So by bringing in these vocal opponents, most of whom have well established blog followings, we will have the opportunity to learn from their experiences, given them some input into the development of The Buccaneer Network and allow them to invite further participants into the closed beta. In this manner, these people become invested in our success while we get to leverage their existing networks. The influence they have over development is then off course confined to The Buccaneer Network, while the trust machine itself will not be affected. For the record, Stack Overflow is currently the 53rd placed global website.
The trust machine link to online identities does not break anonymity or invade user privacy as only trust related data is displayed and no personal details or identifiable traits are passed on to other users of The Buccaneer Network (or any other client system of the trust machine). The net result is that site users get a valid and current indication of each other’s trustworthiness, while each individual user still maintains full control over their own online persona.
Amazon scams on the rise in 2017 as Fraudulent Sellers Run Amok and Profit big. there are 529 counts of negative feedback from people who never received their purchases from one of the three fraudulent sellers (EVILLE, xkuehns,HJSGHUY).https://www.forbes.com/sites/wadeshepard/2017/01/02/amazon-scams-on-the-rise-in-2017-as-fraudulent-sellers-run-amok-and-profit-big/#79b2e6cf3ea6 Continue reading
The success of any large, and/or challenging software engineering project depends to a great extent on the use of a software development methodology. Using a well thought out methodology allows an ordered systematic development of the product. It creates a working environment in which each team member can communicate using a vocabulary defined by the methodology. It also facilitates the development in an ordered way with clearly defined stages which can be monitored communicated and managed to produce the end product robustly and efficiently. Continue reading
It might be blindingly obvious that technology is impacting on every aspect of modern life in most countries. Less obvious thought is the manner in which the world of work is being redefined on an ongoing basis. Automation has for many decades now taken over lower skilled and repetitive tasks while simultaneously creating higher value positions for humans to fill. Over the past decade or so though, the rate of job replacement has increased significantly with machines and software being ever more capable of replacing human workers. It is no wonder then that we see an increasing number of people taking on multiple jobs especially in what is known as the gig economy. Not all digital workers take this route though, with many opting to either take on freelancing for direct clients or venturing into internet marketing. Freelancers in this instance are different from gig workers in that they gain assignments directly from their clients (usually via online communities), typically have substantial experience in the field concerned and earn higher rates per hour. Internet marketers on the other hand, are not old school marketing professionals trying to do online branding. Instead they are self-employed individuals who make some or all of their income, by selling goods and services online.
These are an initial set of functional requirements for the Trust Machine. In keeping with Agile software development principles these will be modified and developed on a regular basis throughout all phases of the development as a result of meetings with stakeholders. These meetings should ideally occur on a weekly basis at the very least and will review the requirements as a priority objective at each meeting. Continue reading
Our tenth meeting contained discussion of wrapping up the blog in time for the deadline.
We had a brief informal meeting last week to catch up after the easter break.
Meeting 10: 3rd May
In this short video, I discuss some of the main requirements for an implementation technology, and also discuss three potential approaches to building the Buccaneer network.
Here are some main pages draft design, aimed at better User Exprience.
Alexander

Meet Alexander
It is all too tempting to add this one to the long list of potential initial expenses, chalk it up to something the investors can pay for and move on to the important stuff. Of course this approach is wrong on every possible level, branding is important, equity is the most expensive form of financing – less is better– , and paying upfront without collecting any pertinent data goes against the grain of the can do spirit at the heart of internet marketing. For The Buccaneer Network at the very least then, simply outsourcing branding to an agency would be a bad route to take. Instead, we propose to use a standard approach from the internet marketing community namely, A/B split testing.
Below is a UML Use-case diagram for the Trust Machine. It has three actors: Continue reading
As I was going back to China, the team mentioned about social networking used to maintain connection during the Easter Vacation. The first thing comes to our mind was using Facebook. However, when I told that Facebook was blocked in China, they were shocked. ‘Then what social networking platform you have?’ this question came next. Actually, not only Facebook, all the products related to Google are not accessible in China, instead, we get chatting software QQ, Wechat to contact with family members, friends and anyone we already know of or familiar with. We get Weibo to link to people we never meet but we interest in or interest in us. What’s more, BaiduTeiba is a good place for us to post our own opinion to the public and get response from every corner. As China has a large population cardinality, the social networking we use ‘internally’ work for enough users’ supporting. Continue reading
Considering the alternatives:
Easy access to near limitless data is one of the key features of the information age. Unfortunately, this superficial truth belies the complexities of freely obtained data. These may include the quality of the data, the direct applicability thereof, how recent it is, who is providing it or how it was obtained. There are numerous other considerations all of which may impact on a specific data use and whether or not any one consideration is of concern will be highly dependent on the situation being addressed. So for instance, a fashion blogger might make good use of data on the shopping habits of a hand full of celebrities. If however the same dataset was presented to the chief procurement officer of an budget clothing retailer, that information would be far from sufficient for planning the next season’s line-up. Continue reading
In order for us to produce the metrics we require we need to understand the various types and models of trust and algorithms available. Continue reading
Trust, a word we use in place of trustworthiness comes in many flavours which have a bearing on how we calculate and quantify it.
Trust can be divided into two ‘top’ catagories. Continue reading
One of the methods we propose for building our trustworthiness metric is to establish a single identity for our users by linking their Trust Machine identity to their other online identities on sites such as Ebay, Facebook and Twitter. The aim is to link an account to one on another service and only allow one link per Trust Machine user, so that once a profile has been used to create a Trust Machine account it can never linked to another one. Continue reading
Further to my recent post on deriving who our target users are, in this blog post I have formulated this into a more ‘formal’ stakeholder analysis.
Later in the blog we will look at some Personas of the stakeholders we have identified. Personas are useful to give realistic, yet totally fictitious, representations to help get inside the mind of the person the system is being designed for. Continue reading
It’s important to make sure that we understand who our target audience are to make sure that we design a product that completely and exactly meet their needs. In this case our product is the Buccaneer social network, which will be free for all to use. Continue reading
Our ninth meeting was slightly shorter than usual, and we talked about our plans for the Easter vacation.
Meeting 9: 23rd March
Our project has two inter-dependant components, both of which are vital to each other. The web application is a business case that we have identified as having immense potential but one that fails because for lack of an effective user trust model. The trust application solves this problem but cannot be built without a use case to build it around and demonstrate its viability. This puts us in the enviable position of having two excellent products for the price of one!
However they will only be excellent if we choose the right technology stack… Continue reading
Trust is concept that exists across numerous disciplines. One thing they all seem to agree on is that there is a lack of agreement either within or across disciplines on what the definition of trust is. One sociologist, Beatty, who declines to settle on a definition, describes it as a mercurial, context-dependent concept defined as a noun, verb, psychological state, personality state, belief, social structure and behavioural intention. Continue reading
A substantial part of this project is the design of a trust framework: a software system for calculating a metric for trust between entities in a social network. In this post we will begin to explore our understanding of trust by looking at it from various academic viewpoints.
In order to make development of the prototypes easier, we requested a virtual machine from the University which will act as our development web server. The prototypes will appear on the server.
How do I access it, I hear you cry?
You need to be inside the University VPN or actually using a computer inside the University network. Then, simply navigate to:
svm-gc5g13-buccaneer.ecs.soton.ac.uk
And as soon as a web page is available, this is where you will see it. The domain name isn’t pretty, but at the end of the day it’s there so we can easily share our prototypes!
Today we discussed mainly work on the blog, and started to think about longer term action points and what we wanted to achieve before the easter break.
Meeting 8: 16th March
Today we discussed who our potential users might be, and also explored some potential functionality.
Meeting 7: 14th March
The social network space for online marketers is dominated by two major players, Warrior forum and Blackhatworld. As the names might suggest, these communities do not present themselves as warm and caring spaces but are instead all about doing the best deals, often at any cost. This is not to say that there aren’t helpful individuals participating or that the content is universally suspect, but rather that the pervasive attitude amongst users is one of “trust no one and test everything twice before use”. As anybody with an entrepreneurial background would know, this type of environment is massively inefficient and would necessitate the introduction of checks that go beyond standard due diligence. One quick test yielded a time to implementation for an SEO technique at three times what it would have been had the information come from a different source. Continue reading