We have a prototype!
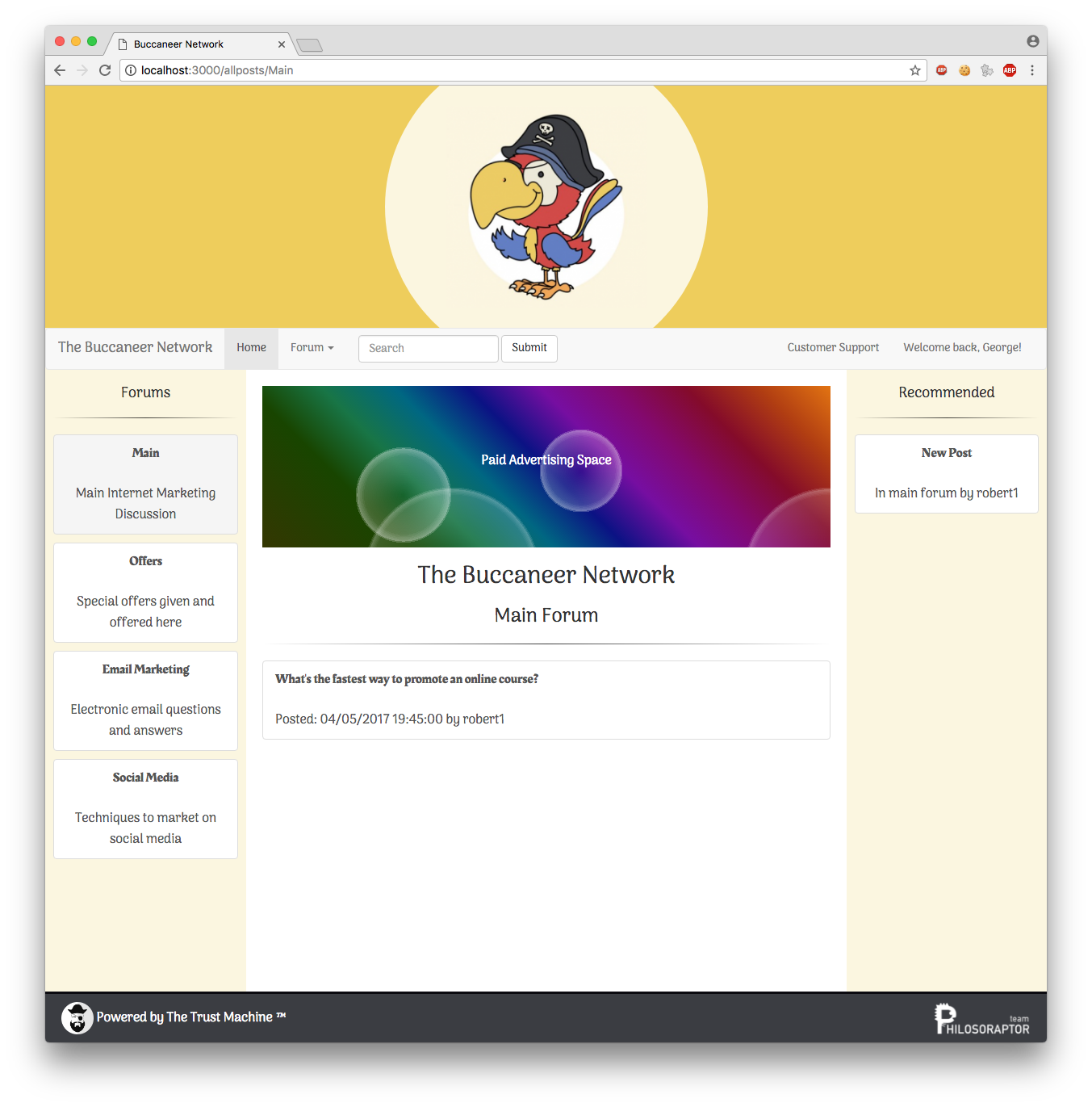
This mock up is a very, very basic mock-up of what could be achieved if this project were to go ahead.
You can visit it here.

We have a prototype!

This mock up is a very, very basic mock-up of what could be achieved if this project were to go ahead.
You can visit it here.
Trust, as we have seen, is a complex thing to model. To quantify it we need to look at a variety of parameters e.g. User behaviours, user provenance and user context. Each of these parameters will modify the trust value. However not all will be used in every setting. We will need different flavours of trust calculation and ways of keeping track of which was used to construct each trust calculation. Designing code to implement a complex model of trustworthiness is going to be a challenge, particularly if we want maintainable code built along proper Object Oriented design principles. Continue reading
By the time The Buccaneer Network launches it will already have a thriving community and the trust machine will be actively disrupting the industry. We will accomplish this in two ways. Firstly, we will take a page out of Stack Overflow’s playbook and build a solid community before the official launch. We will do so by inviting some of the most outspoken opponents of the incumbent operators to take part in our closed beta. At a very general level people automatically support that which they had a hand in creating. So by bringing in these vocal opponents, most of whom have well established blog followings, we will have the opportunity to learn from their experiences, given them some input into the development of The Buccaneer Network and allow them to invite further participants into the closed beta. In this manner, these people become invested in our success while we get to leverage their existing networks. The influence they have over development is then off course confined to The Buccaneer Network, while the trust machine itself will not be affected. For the record, Stack Overflow is currently the 53rd placed global website.
The trust machine link to online identities does not break anonymity or invade user privacy as only trust related data is displayed and no personal details or identifiable traits are passed on to other users of The Buccaneer Network (or any other client system of the trust machine). The net result is that site users get a valid and current indication of each other’s trustworthiness, while each individual user still maintains full control over their own online persona.
Amazon scams on the rise in 2017 as Fraudulent Sellers Run Amok and Profit big. there are 529 counts of negative feedback from people who never received their purchases from one of the three fraudulent sellers (EVILLE, xkuehns,HJSGHUY).https://www.forbes.com/sites/wadeshepard/2017/01/02/amazon-scams-on-the-rise-in-2017-as-fraudulent-sellers-run-amok-and-profit-big/#79b2e6cf3ea6 Continue reading
The success of any large, and/or challenging software engineering project depends to a great extent on the use of a software development methodology. Using a well thought out methodology allows an ordered systematic development of the product. It creates a working environment in which each team member can communicate using a vocabulary defined by the methodology. It also facilitates the development in an ordered way with clearly defined stages which can be monitored communicated and managed to produce the end product robustly and efficiently. Continue reading
It might be blindingly obvious that technology is impacting on every aspect of modern life in most countries. Less obvious thought is the manner in which the world of work is being redefined on an ongoing basis. Automation has for many decades now taken over lower skilled and repetitive tasks while simultaneously creating higher value positions for humans to fill. Over the past decade or so though, the rate of job replacement has increased significantly with machines and software being ever more capable of replacing human workers. It is no wonder then that we see an increasing number of people taking on multiple jobs especially in what is known as the gig economy. Not all digital workers take this route though, with many opting to either take on freelancing for direct clients or venturing into internet marketing. Freelancers in this instance are different from gig workers in that they gain assignments directly from their clients (usually via online communities), typically have substantial experience in the field concerned and earn higher rates per hour. Internet marketers on the other hand, are not old school marketing professionals trying to do online branding. Instead they are self-employed individuals who make some or all of their income, by selling goods and services online.
These are an initial set of functional requirements for the Trust Machine. In keeping with Agile software development principles these will be modified and developed on a regular basis throughout all phases of the development as a result of meetings with stakeholders. These meetings should ideally occur on a weekly basis at the very least and will review the requirements as a priority objective at each meeting. Continue reading
Our tenth meeting contained discussion of wrapping up the blog in time for the deadline.
We had a brief informal meeting last week to catch up after the easter break.
Meeting 10: 3rd May
In this short video, I discuss some of the main requirements for an implementation technology, and also discuss three potential approaches to building the Buccaneer network.
Here are some main pages draft design, aimed at better User Exprience.
Alexander

Meet Alexander